Why Two-Factor Authentication is a Big Factor in Security

In our generation where the internet is almost accessible to anyone anywhere, intruders can be found wherever on the web. Creating fraud accounts, hacking necessary files especially on our personal and financial accounts. As a result, it makes us recognize that having a Username and Password is not enough to secure our accounts from potential attackers. Because in every account we create, we may not be informed that someone is developing a new way to determine our identity using our usernames and passwords.

Internet security is a fragile thing nowadays that there comes to the point of paranoia wherein we are starting to think if we can have a better way of securing our accounts. Something so secure that only the real owner can have access to their accounts. Some of us, especially those who are not frequent internet users, don’t know that having a Username and Password is just the first stage of security that is called “Two Factor Authentication”.
In Two-Factor Authentication, we may have the security that every user wanted because it has steps that needed to be fulfilled before the system grants us access to our accounts.
The first is called “Knowledge”, which is very well known to us as Username and Password. The stage that every internet user must have. It can be also a hint, secret question or anything that only us can remember and never forget. Some people stop at this stage, especially those who do not bother much with security. This is what the attackers can easily have access to.

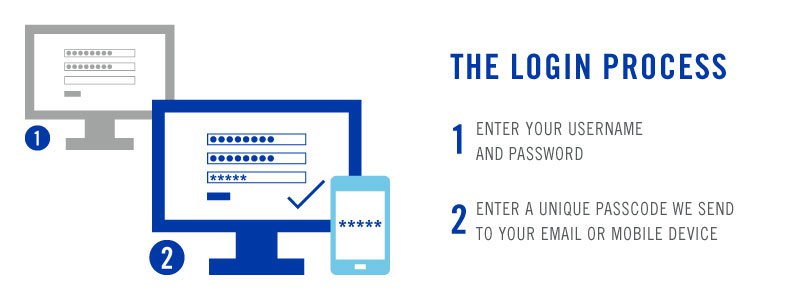
The second stage, which every user should have, is called “Possession”. Something that we, as a user, can carry or will always be carrying. Examples are I.D, ATM card, or mobile phone. A good example and most commonly used in this stage is the mobile phone or e-mail address. At the first part you will login using your Username and Password which is “Knowledge”, and then in the second stage, you will receive the passcode on your mobile phone or e-mail address. Then you will be requested to input the passcode that is sent to your mobile phone/e-mail before you can continue to log in to your account. In this case, even if the attackers know your username or password, they still can’t easily get the access to your account because of the second layer of protection. You will also be aware that someone is trying to login to your account because you will receive a passcode even if you do not seek to log in.
The last stage is “Inherence”. This is the most secure stage and also more expensive as it requires a more advanced equipment to implement. It is the stage where the system is requesting to scan body parts like eye (retina), fingerprints, and such of user’s physical body who’s trying to gain access to his/her account. The said stage is considered as the most powerful way to secure and protect anyone’s private account and credentials since it requires the physical presence of the account holder.

Considering each stage that was discussed about Two-Factor Authentication, we now have options on securing our accounts on a different level.
1 . Knowledge
The stage where we enter only our Username and Password.
2. Possession
The stage where we confirm the login using another device. More commonly used is mobile phone or e-mail.
3. Inherence
The stage where physical presence is required, such as fingerprint or retina scanning.
We, the Portal Integrators Team, have considered these stages and can speak based on experience that those steps are very helpful in protecting our accounts.
Two-Factor Authentication is Advised
Only logging in using Username and Password is not secure enough anymore. If we need a more secure way to protect our accounts, the two-factor authentication can help.
It helps Us Be More Aware
By using two-factor authentication, we can be made aware of scenarios wherein someone else is trying to hack into our account by notifying us of a login attempt and confirmation.
You Can Sleep Easy
Knowing that two-factor authentication secures your accounts, we can sleep better at night.